Difference between revisions of "Setup Secure File Transfers over FTPes"
>Jeremyb (→Setup FTP Server) |
>Jeremyb |
||
| Line 25: | Line 25: | ||
[[File:Vitalsignsftpes10.png]] | [[File:Vitalsignsftpes10.png]] | ||
| − | |||
| Line 99: | Line 98: | ||
[[File:Vitalsignsftpes23.png]] | [[File:Vitalsignsftpes23.png]] | ||
| + | |||
| + | |||
| + | |||
| + | ==Confirm FTPes works== | ||
| + | |||
| + | Use your favorite ftp client that supports FTPes and setup a connection for the new FTPes Server with the following settings : | ||
| + | * FTPes (FTP over SSL/TLS) | ||
| + | * Prot P | ||
| + | * Active (not PASV) | ||
| + | * Port 21 | ||
| + | |||
| + | Try to connect with the client and then review the FileZilla Server logs in the Server | ||
| + | |||
| + | |||
| + | ==Enable FTPes on HPUX== | ||
| + | |||
| + | Once the FTPes server connectivity to an external client has been confirmed, login to the HPUX box as the askplus user and edit /ASKPLUS/vsdata/vitalsigns.ini | ||
| + | |||
| + | Confirm the following FTP settings are appropriate for your setup : | ||
| + | |||
| + | <pre> | ||
| + | FTP_USER=yourftpuser | ||
| + | FTP_PASSWD=yourpassword | ||
| + | FTP_PORT=21 | ||
| + | FTP_PASV=No | ||
| + | FTP_SECURE=Yes | ||
| + | </pre> | ||
| + | |||
| + | |||
| + | Test the nightly run by doing the following | ||
| + | <pre> | ||
| + | login bolive | ||
| + | /VSJOBS/JVSLOAD_HIST | ||
| + | </pre> | ||
| + | |||
| + | Review the stdlist for the following to indicate that the connectivity is secure : | ||
Revision as of 00:00, 14 February 2014
Contents
Summary
How to enable file transfers between the HPUX and Windows Vital Signs server host via FTP over TLS (FTPes)
Setup FTP Server on Windows
Currently as of version 1.6, FTPes is only supported with FileZilla Server for Windows
Download FileZilla Server Here
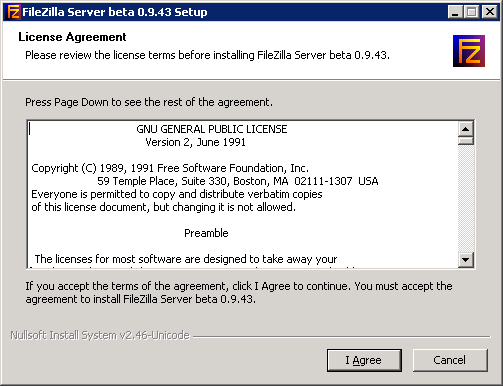
After downloading the file, run the exe on the Windows server where Vital Signs will be hosted to begin the File Zilla Server setup
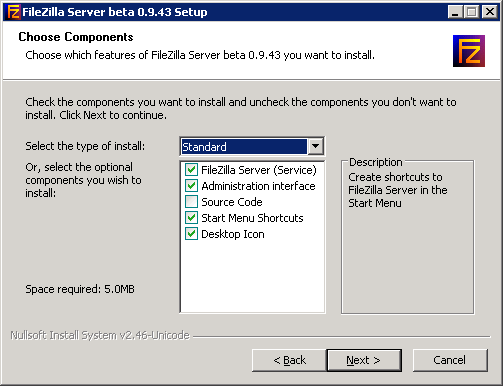
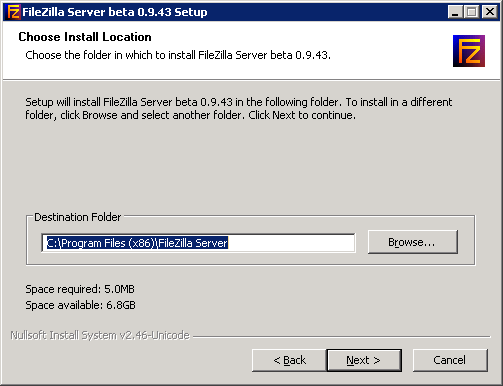
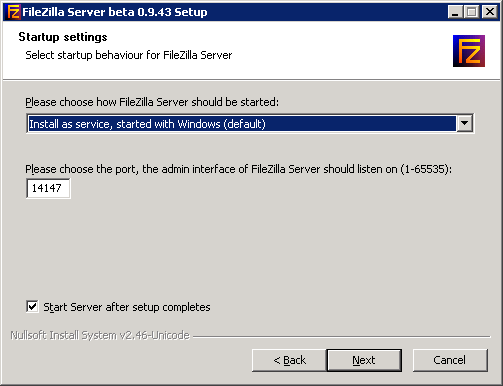
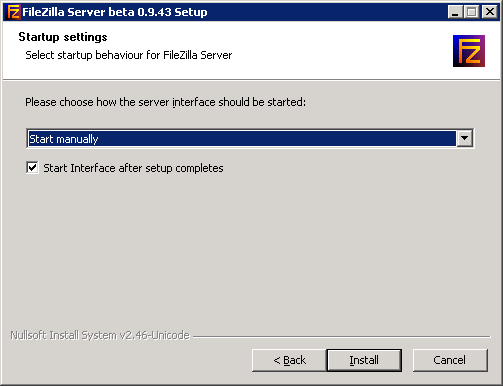
The following are the recommended settings
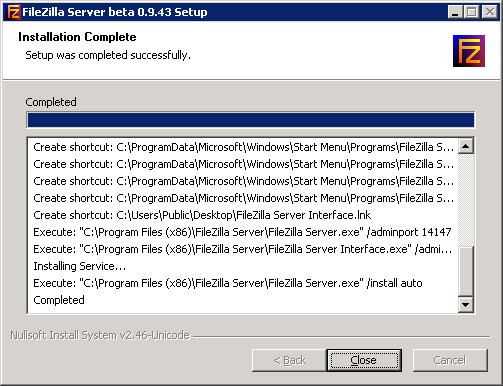
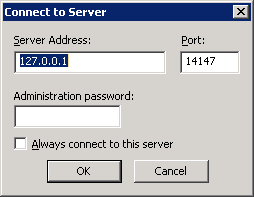
Once the installation is complete, the File Zilla Server UI should prompt to Connect to Server. Click OK
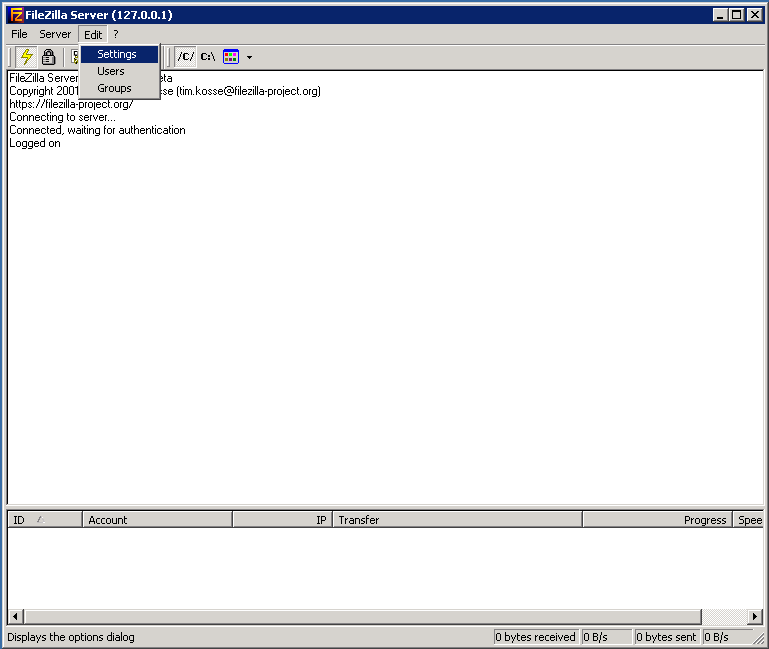
Once logged into the Server UI, select Edit, Settings
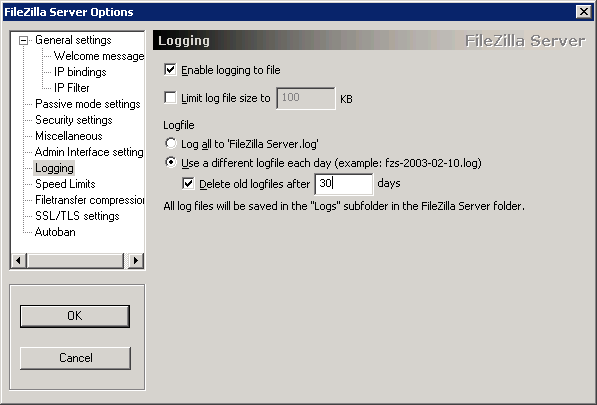
Under Logging, check Enable logging to file and choose to create new log files for each day with 30 days of retention
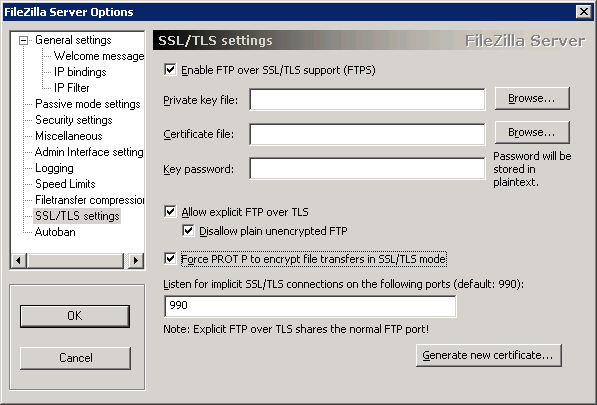
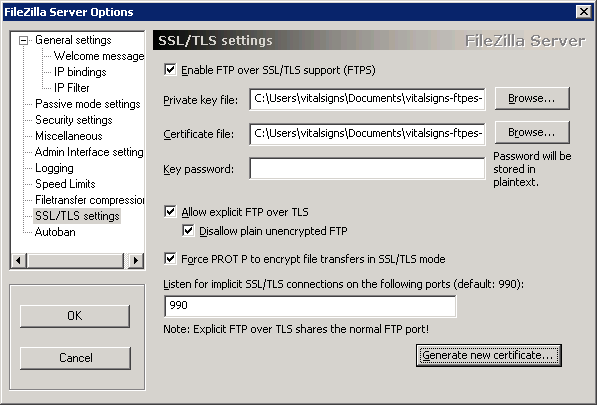
Under SSL/TLS settings, check Enable FTP over SSL/TLS support (FTPS), Allow explicit FTP over TLS, Disallow plain unencrypted FTP and Force PROT P to encrypt file transfers in SSL/TLS mode
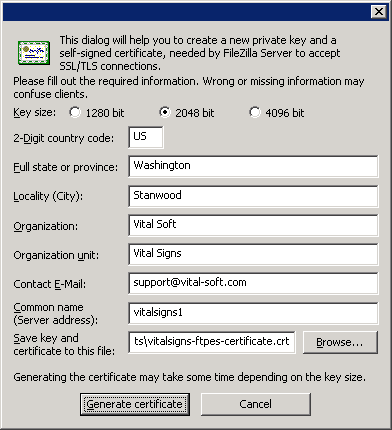
Finally, click Generate new certificate...
Select 2048bit for the key size
Enter the appropriate information for the certificate
Enter a path for the vitalsigns-ftpes-certificate.crt file to be generated in and click Generate certificate
You should now see the Private key file and Certificate file populated.
Click OK
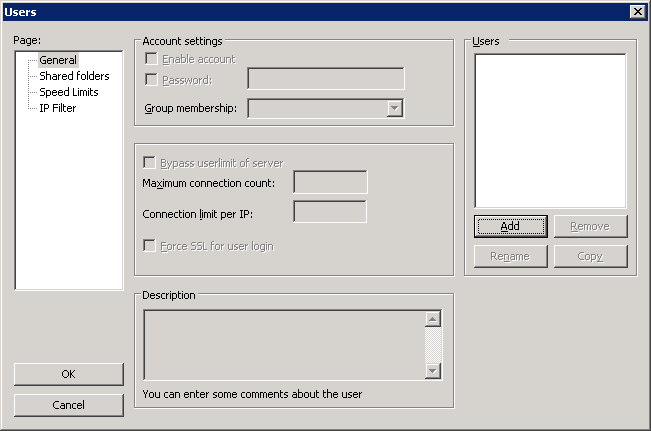
Setup a User
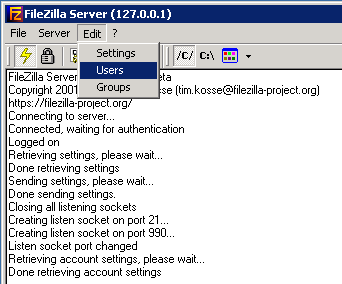
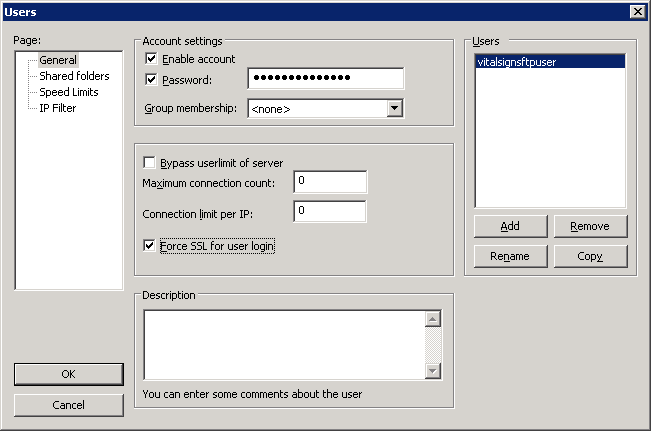
In the FTP Server UI, select Edit, Users
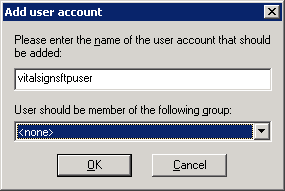
Click Add under Users
Enter the ftp user name and click OK
Click the Password: box and enter the ftp user password
Check the Force SSL for user login and click OK
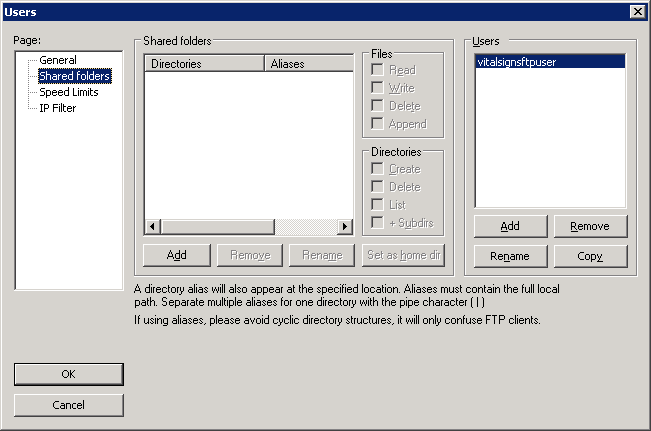
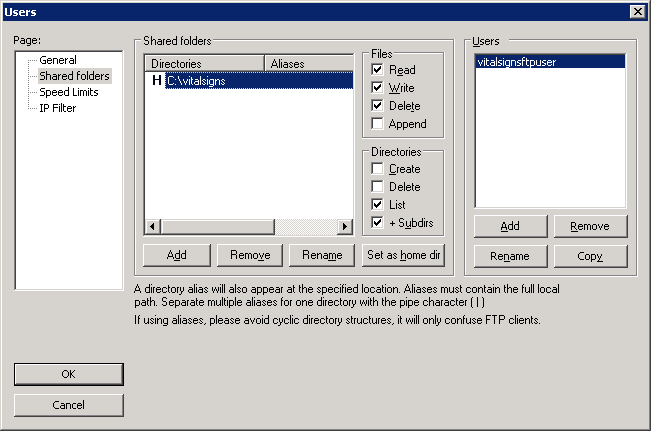
Under the Shared folders, click Add
Select the path to the vitalsigns directory and check the Read,Write and Delete check boxes and click OK
Confirm FTPes works
Use your favorite ftp client that supports FTPes and setup a connection for the new FTPes Server with the following settings :
- FTPes (FTP over SSL/TLS)
- Prot P
- Active (not PASV)
- Port 21
Try to connect with the client and then review the FileZilla Server logs in the Server
Enable FTPes on HPUX
Once the FTPes server connectivity to an external client has been confirmed, login to the HPUX box as the askplus user and edit /ASKPLUS/vsdata/vitalsigns.ini
Confirm the following FTP settings are appropriate for your setup :
FTP_USER=yourftpuser FTP_PASSWD=yourpassword FTP_PORT=21 FTP_PASV=No FTP_SECURE=Yes
Test the nightly run by doing the following
login bolive /VSJOBS/JVSLOAD_HIST
Review the stdlist for the following to indicate that the connectivity is secure :